Delivery Services
Vendor Management
As critical corporate services shift out to the cloud, third parties have a greater impact on the operational effectiveness of nearly every business. Driving service excellence, controlling costs, mitigating risks and reaching internal targets require a new set of business processes, skills and resources. You need to know the right questions to ask target vendors, then identify which are right for your specific business. You also need to have the right controls in place to have companies deliver as promised. With two decades of experience in all areas of vendor management, from prioritizing client needs to contract development to implementation oversight, we will be the eyes and ears to oversee these organizations and deliver the expected benefits.
Sourcing, selecting and managing suppliers is a time-intensive requirement that can eat up a company’s most valuable resources. Even though senior executives should focus on the main components driving revenues and increasing profits, they know that without the right oversight with critical partners, the company can be exposed to a great deal of risk. We hope that others will not violate the trust given to them, but too often this agreement is broken when firm’s hand over operational duties. Therefore, you need to have a governance model in place that will enable you to work with your partners effectively.
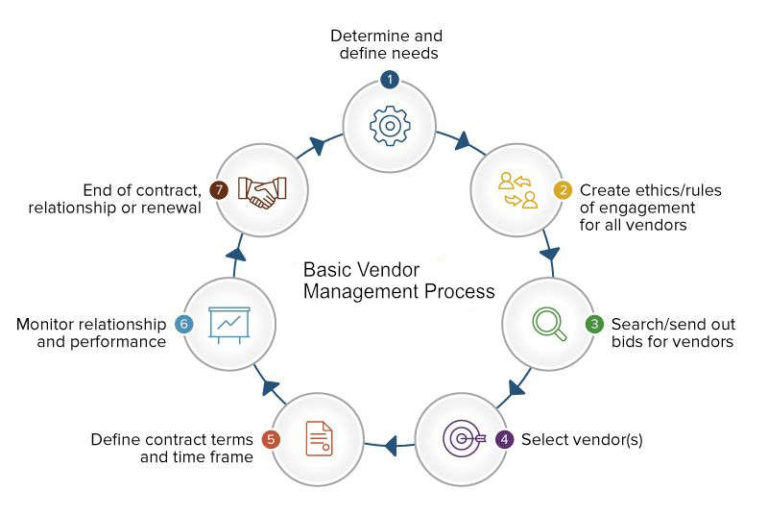
For vendor risk management to be successful, there are some basic best practices that should be followed:
1. Create partnership agreements in multiple dimensions: Have a service level agreement that is written and / or reviewed by your legal team (and not through the vendor). Establish the time frames, performance measurements, liabilities and punitive damages for a violation of the agreement. Spell out all checkpoints, scheduled milestones, on-going deliverables, and how they will be measured.
2. Provide, and expect, full transparency: Third parties should know what you expect of them, and when, so that they can meet the terms of the agreement. No vendor should have to guess what actions or accesses might pose a risk. At the same time, you should have an agreement with them that implies they will do the same, whether it is implicitly in an agreement. For example, if there was a potential data breach, but not on a public platform such as a web-server, you should expect them to come forward as soon as possible.
3. Agree on Risk Responsibility and Mitigation: Decide early on how risks will be identified, monitored, and reviewed. Agree on the plan to keep the risks in check, and who is responsible for handling it if a risk should turn into a major issue.
4. Consistency: Breaches by vendors almost always are caused by a failure to enforce already-existing rules and protocols. Continuous checks by internal teams as well as external audit groups can ensure processes are followed to protect critical information.
5. Ongoing Relationship Management: Cover every step of the relationship, from the bidding process through termination of project and relationship.
We can bring a combination of experience, knowledge and tools customized for large-scale implemenations. By combining these with best practices learned over twenty years, the benefits realized outweigh the out-of-pocket investment.
